A Long History of Mathematical Trust
Cryptography is not a new field. It has existed for thousands of years. There has always been a need to keep secrets and encrypt messages, mainly for military and political reasons, but also for commercial and industrial confidentiality.
However, the goals and methods of cryptography have evolved over time, and since the introduction of networked computing, it has become incredibly versatile. Powerful cryptography is now readily available to anyone and, in fact, used by most people on a daily basis without them even realizing it. However, it is also increasingly difficult for companies to use cryptography effectively. In fact, it has become a real challenge to configure cryptographic protocols correctly and use them with secure parameters, even for experienced software developers.
SylLab Systems advocates outsourcing cryptography to professional services and allowing enterprises to focus on their core business. However, we also believe that a basic understanding of how cryptography works is beneficial.
In this article, we discuss the evolution from classic cryptography that focused on transmitting secrets securely to modern, computerized cryptography that pretends to provide mathematically backed trust and privacy on information and data sources.
Classic Cryptography

Initially, the main purpose of cryptography was to encrypt messages, so that they cannot be read by anyone apart from the intended recipient. The sender scrambles or transforms the message applying some secret knowledge, commonly called the key. The receiver can apply the same key to decipher the message. Should the message fall into the hands of someone else, it should be meaningless to them without the secret key.
This type of cryptography, when applied to text messages and before the invention of modern computers, is commonly known as classic cryptography and has existed for a long time. The Caesar Cipher, used in Roman times, is a good example of earlier cryptography.
Classic cryptography reached its peak during world war two with the German Enigma machine, used to encrypt military messaging. This type of cryptography typically works on text, scrambling it, in order to make it only legible to someone in possession of a secret key.
Modern Cryptography
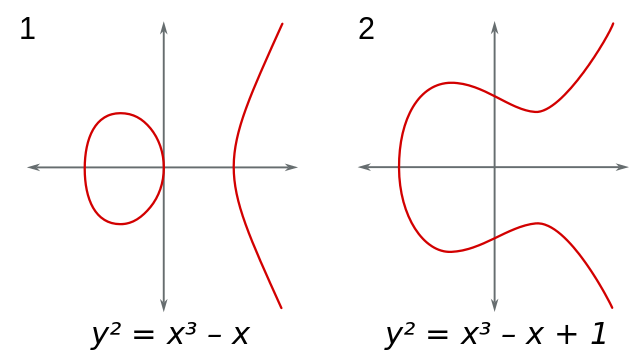
With the invention of computers, cryptography also changed forever. Suddenly complex mathematical operations could be performed to increase the security of ciphers. To this end, modern cryptography, in contrast to its classic counterpart, operates on numbers instead of text. This can be achieved because any type of information can easily be encoded as numbers. In fact, anything stored in computer systems has to be represented as a number.
Computing power and mathematical complexity have also allowed cryptography to be used for applications that go well beyond simple encryption. Many forms of cryptography exist, but their goals can be classified using the following three desired properties:
- Confidentiality: This is the property carried over from classical cryptography. It centers on keeping a message secret. Like in classic cryptography, secret keys are used to scramble a message on the sender’s side and to unscramble it on the receiver’s end. The main difference to classic cryptography is that messages are scrambled using mathematical operations over numbers. This can be done in many ways, either on blocks of data (block cipher), for example on data stored in a database, or in real-time on streamed data (stream cipher), such mobile phone conversations.
- Integrity: It is often of interest to ensure that a message or data has not been altered or tampered with. This integrity property is useful for encrypted data, but also for unencrypted data, as there are plenty of cases in which data should be public but protected from unauthorized alterations. Hashing algorithms, which calculate a unique digital fingerprint of a piece of data, are an example of this.
- Authenticity: The third objective of modern cryptography is to ensure that the source of a message can be clearly identified. What this means is that the receiver can be sure who the sender of the received message is.
Different cryptographic tools may focus on different combinations of these properties. Digital signatures, for instance, are a tool of modern cryptography that combines the latter two properties. The signer of a piece of data can be identified (authenticity) and any modification of the data can also be detected easily (integrity). If confidentiality is also required, the signed data can be encrypted.
Securely Exchanging the Key
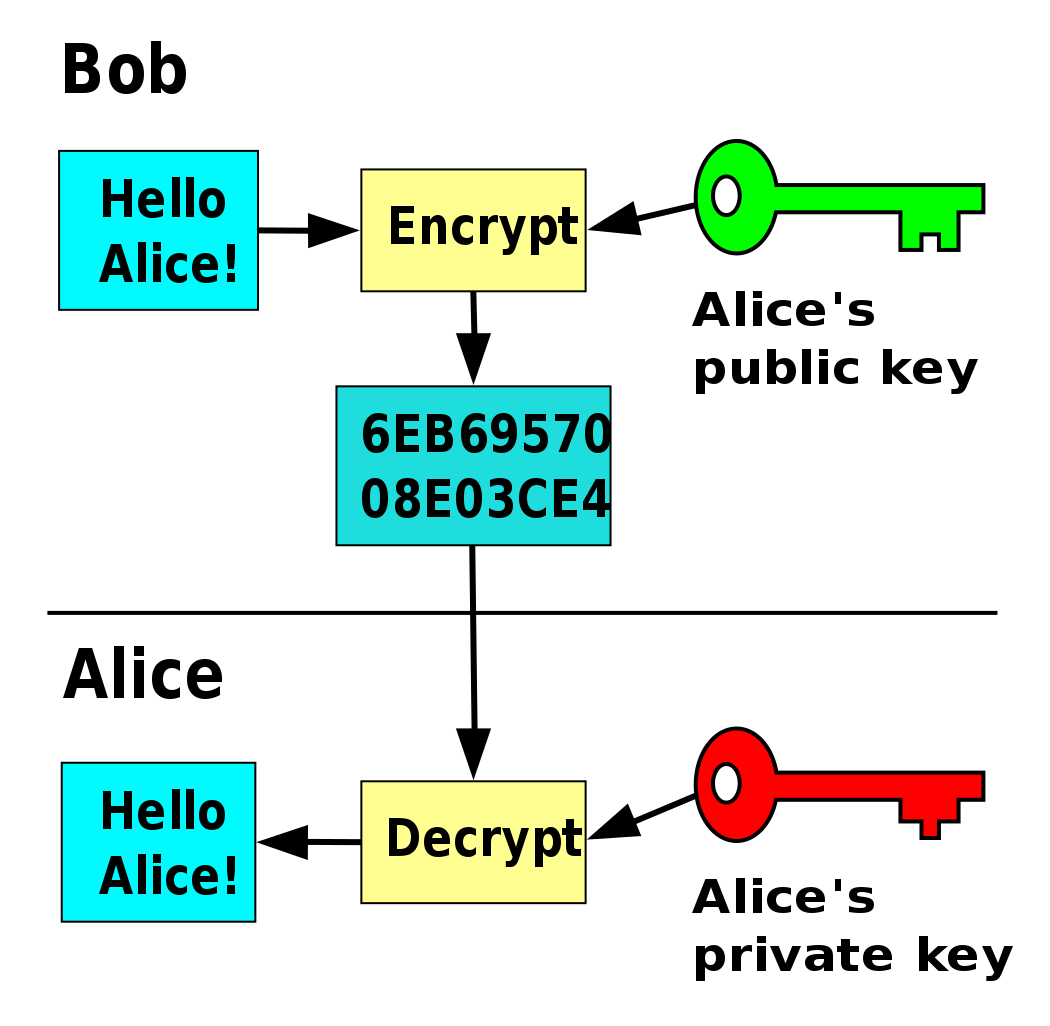
The invention of computers may have provided the advanced computational capacities that allow complex mathematics to be used for cryptography, but modern cryptography really came into its own in the 1970s, when a remaining problem was solved by asymmetric cryptography. This problem consists of making sure the sender and receiver of a message can agree on the secret key to encrypt and decrypt the message. It is inherently difficult to agree on a key securely in a networked environment without transmitting the key offline since any cleartext message containing the key could be intercepted.
Asymmetric cryptography solves this issue by using different keys for encryption and decryption. Keys exist in pairs, a public key and a private key. The public key, as the name suggests, is public and can be freely shared. It is used to encrypt a message for a receiver. The private key, on the other hand, is secret and can be used to decrypt messages encrypted with the corresponding public key. Of course, public and private keys are mathematically related, but it is close to impossible to derive the private key from the public key.
Using this system is reverse, gives rise to digital signatures. If a message is signed with a private key, the sender can be verified using the corresponding public key.
Asymmetric encryption enables applications, such as secure website connections and, basically any form of secure communication channel that has to be established over a network. We will take a closer look at how asymmetric cryptography works in detail in a future article.
Modern cryptography can, of course, provide further properties, besides those mentioned above. Depending on its application cryptography can take on many variants. This highly complex mathematical discipline can be hard for companies to navigate but cannot be ignored in the modern connected world.

